GSoC2018:Trust-based routing protocols framework
Main Page - Roadmap - Summer Projects - Project Ideas - Developer FAQ - Tools - Related Projects
HOWTOs - Installation - Troubleshooting - User FAQ - Samples - Models - Education - Contributed Code - Papers
Return to GSoC 2018 Accepted Projects page.
Project Overview
- Project name: Trust-based routing protocols framework
- Student: Jude Niroshan
- Mentor: Tommaso Pecorella
- Abstract: ns-3 contains different routing modules, both for IPv4 and for IPv6. None of them are trust-based routing protocols. Given the increasing interest on trust-based routing schemes to increase and improve the network resilience vs routing attacks, it would be useful to have a general approach for trust-based schemes. As a matter of fact, there are multiple trust-based extensions for well known protocol (e.g., AODV), but each one modifies in a particular way the single routing protocol, making it difficult to export the solution to other routing schemes. Therefore, it would be beneficial for many developers to have a generic trust-based framework which accommodates the alteration of well-known protocols to work as trust based protocols.
- Code: Github repository
- About me: I am an undergraduate student at the Sri Lanka Institute of Information Technology(SLIIT), Sri Lanka. I'm so excited to work with ns-3 community during the summer of 2018. You can find more about me on LinkedIn
Introduction
Networks are susceptible to attacks by malicious nodes that could easily bring down the whole network. Therefore, it is important to have a reliable mechanism for detecting and isolating malicious nodes before they can do any harm to the network. Usually, routing protocols discover usable multi-hop routes between source and destination nodes. However, some of the routes found and used may not be as reliable or trust-worthy as expected. Thus, finding a trusted route is an important component for enhancing the security of communication. Enhanced trust and security are achieved by the maintenance of a trust factor by the nodes in the network. This factor is established and refined over time and it increases for each node when it participates successfully in data transmissions.
What is the Trust value
Trust is a relationship established between two entities for a specific action. In particular, one entity trusts the other entity to perform an action. In this work, the first entity is called the subject, the second entity is called the agent.' [1]
Trust is a function of uncertainty. In particular, if the subject believes that the agent will perform the action for sure, the subject fully “trusts” the agent to perform the action and there is no uncertainty; if the subject believes that the agent will not perform the action for sure, the subject “trusts” the agent not to perform the action, and there is no uncertainty either; if the subject does not have any idea of whether the agent will perform the action or not, the subject does not have trust in the agent. In this case, the subject has the highest uncertainty.[1]
Trust value should represent uncertainty.[1] Uncertainly always stick to the probability which always has the value ranging from 0 - 1. Therefore, trust value will also be ranging from 0 - 1 by denoting the trust between nodes in the network.
- [1] Sun, Y.L., Yu, W., Han, Z. and Liu, K.R., 2006. Information theoretic framework of trust modeling and evaluation for ad hoc networks. IEEE Journal on Selected Areas in Communications, 24(2), pp.305-317.
Why need a trust based framework
Trust is a subjective measurement. There are many research papers have published which has various methodologies of calculating the trust value for the same routing protocol.
For e.g.: If we consider AODV routing protocol; following papers have came up with different approaches for trust value calculation.
- [2] Li, X., Lyu, M.R. and Liu, J., 2004, March. A trust model based routing protocol for secure ad hoc networks. In Aerospace Conference, 2004. Proceedings. 2004 IEEE (Vol. 2, pp. 1286-1295). IEEE.
- [3] Marchang, N. and Datta, R., 2012. Light-weight trust-based routing protocol for mobile ad hoc networks. IET information security, 6(2), pp.77-83.
- [4] Pushpa, A.M., 2009, December. Trust based secure routing in AODV routing protocol. In Internet Multimedia Services Architecture and Applications (IMSAA), 2009 IEEE International Conference on (pp. 1-6). IEEE.
NS-3 cannot define only one way of calculating trust value as each of these methods/approaches have written to serve specific concerns/issues. Therefore, it is clear that allowing any custom trust calculation as a framework is a better move from NS-3. This will help the developers to try out trust based frameworks in NS-3 with minimal amount of coding.
Technical Approach
As of now NS-3 does not support to simulate the above mentioned trust based routing protocols. If somebody wants to simulate such an environment, there are lot of changes needs to be done in many concrete classes. This is cumbersome and it is against the conventions that we follow from the maintainence point of view. Therefore, this project is aimed to facilitate a new trust module which enables the capability of implementing a trust based algorithm to NS-3 and let the users to tryout the simulations based upon them.
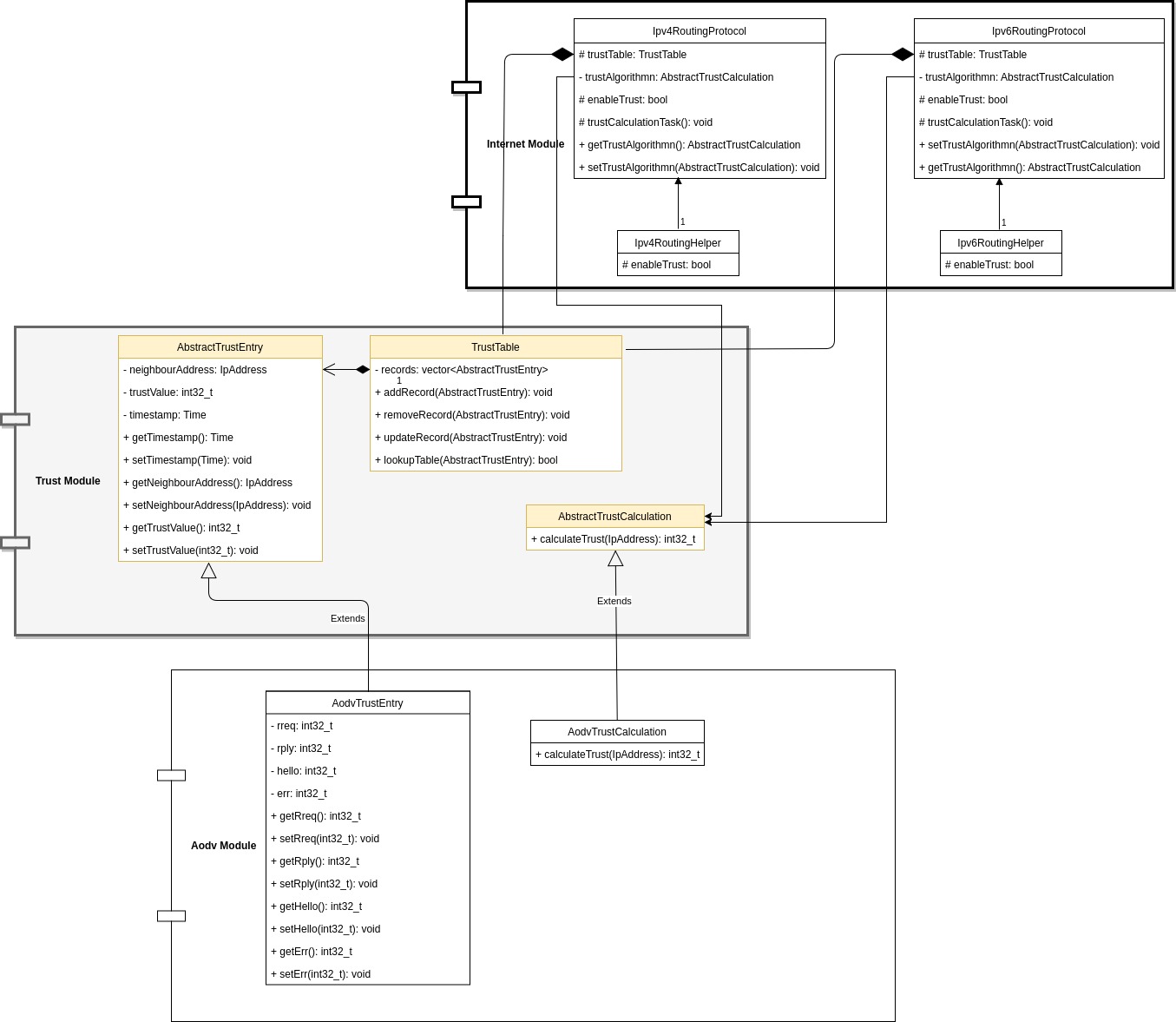
New trust module consists of abstract classes which can be extended and implemented as the user's preferences. Users can extend the AbstractTrustCalculation class and implement their own logic to calculate the trust measurement.
TrustTable is a new table which is similar to routing table. Trust table contains trust value related information for directly connected nodes. Users will be able to add new properties to trust table as they wish. At the same time, trust calculation logic is also feasible to change according to the above framework structure. As you can in UML, any user can define the trust calculation algorithm by simple extending the AbstractTrustCalculation class.
Project Timeline
Week 1 (May 14 - May 20)
- Clone appropriate git repository
- Investigate on the internal and external network attack types
Week 2 (May 21 - May 27)
- Create a well structured UML diagram
- Create a simple simulation with 2 network nodes. Analyze the data packets that transfer between those nodes.
- Create the Abstract trust table class
Week 3 (May 28 - June 3)
- Create a new ns-3 module called 'trust'
- Move abstract classes into that new module and test (Done, but raised dependency issues)
Week 4 (June 3 - June 10)
- Write up a trust implementation before making a abstract module
- Test the AODV specific implementation
Week 5 (June 11 - June 17)
- Write doxygen documentation for abstract classes implemented inside internet module
abstract-trust-entry.h
abstract-trust-calculation.h
trust-table.h
ipv4-routing-helper.h
- Modify the helper classes to place the main boolean flag to turn on or off the trust based framework
Ipv4RoutingHelper::Ipv4RoutingHelper (bool enableTrust)
{
this->enableTrust = enableTrust;
}